FlexDeploy - Terraform Plugin Guide
Operations for planning, applying or destroying Terraform resources. Supports local file system state or back end state managers such as Consul. Plugin supports FlexDeploy Cloud Accounts for the following providers; AWS, Azure, and Oracle Cloud Infrastructure. You can specify a Cloud Account which will handle all necessary authentication and connection information for you. If you wish to use another provider the authentication must be handled separately.
Validated Versions
- v0.11.13
Key Features
- FlexDeploy Cloud Account configuration support for AWS, Azure, Oracle Cloud Infrastructure
- Back end and local state support
- Terraform variable and output support
- FlexDeploy property replacement
Recommendations
State
While local state is supported, it is recommended to use a back end state manager such as Consul for robust visibility and persistence.
Consul is provided by HashiCorp, and like Terraform it is also available for free download.
Plugin Operations
Cloud Accounts and Authorization
Supported Cloud Accounts
- AWS
- Microsoft Azure
- Oracle Cloud Infrastructure
Creating Authorization for other Providers
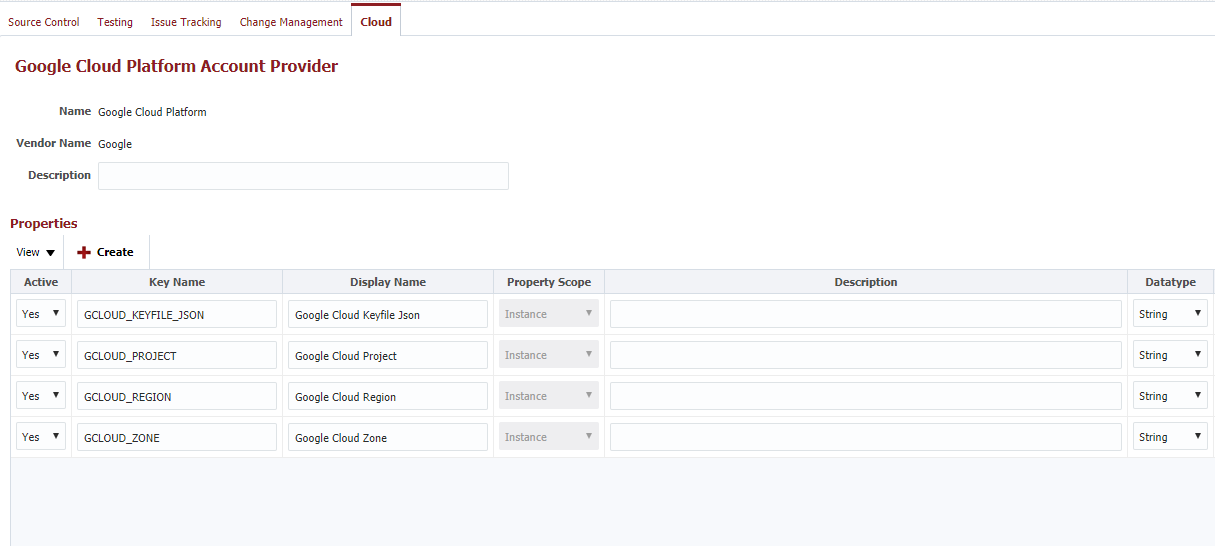
If you wish to use a Provider not in the above supported list you can authenticate using traditional Terraform standards. This usually results in either environment variables for authentication information or having this information directly in the Terraform files. If you wish to use the latter approach you can create a custom FlexDeploy Cloud Account Provider.
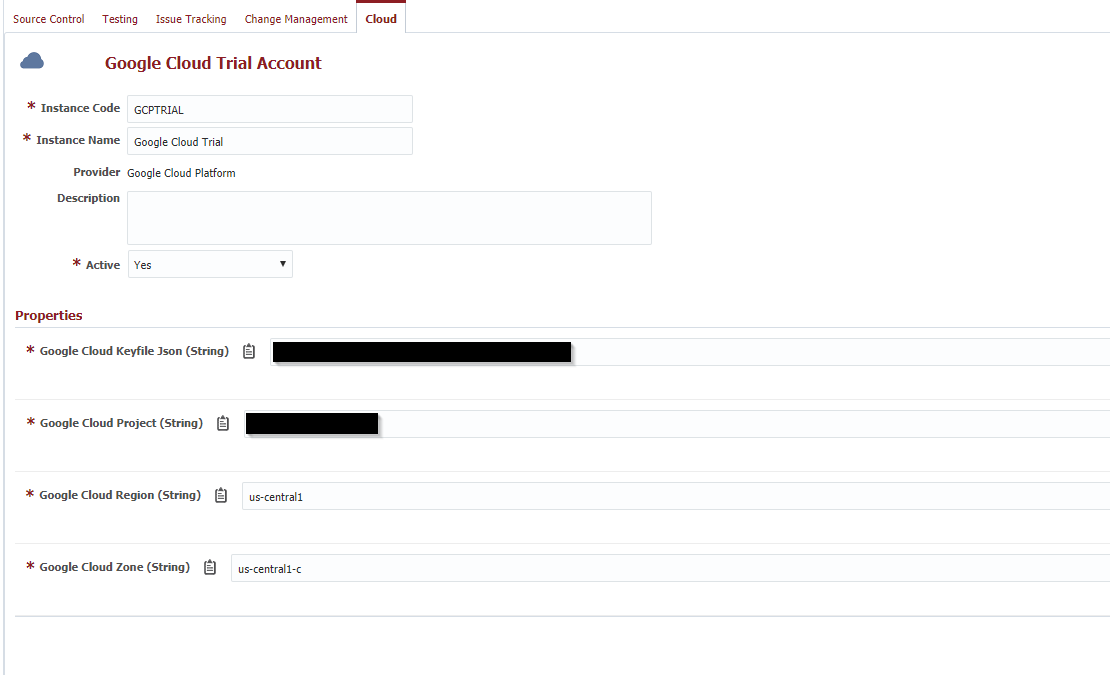
You can then reference the values on the Cloud Account using FlexDeploy properties in your Terraform configuration files. Below I have demonstrated with the Google Cloud Platform provider:
FlexDeploy Provider (Google Cloud Platform)
Flexdeploy Account (Google Cloud Platform)
Terraform Configuration (Google Cloud Platform)
provider "google" {
credentials = "${file("${{GCPJOEL:GCLOUD_KEYFILE_JSON}}")}"
project = "${{GCPTRIAL:GCLOUD_PROJECT}}"
region = "${{GCPTRIAL:GCLOUD_REGION}}"
zone = "${{GCPTRIAL:GCLOUD_ZONE}}"
}
resource "google_compute_instance" "vm_instance" {
name = "terraform-instance"
machine_type = "f1-micro"
boot_disk {
initialize_params {
image = "debian-cloud/debian-9"
}
}
network_interface {
# A default network is created for all GCP projects
network = "${google_compute_network.vpc_network.self_link}"
access_config = {
}
}
}
resource "google_compute_network" "vpc_network" {
name = "terraform-network"
auto_create_subnetworks = "true"
}
Related content
- style