...
| Child pages (Children Display) |
|---|
Cloud Accounts and Authorization
Supported Cloud Accounts
- AWS
- Microsoft Azure
- Oracle Cloud Infrastructure
Creating Authorization for other Providers
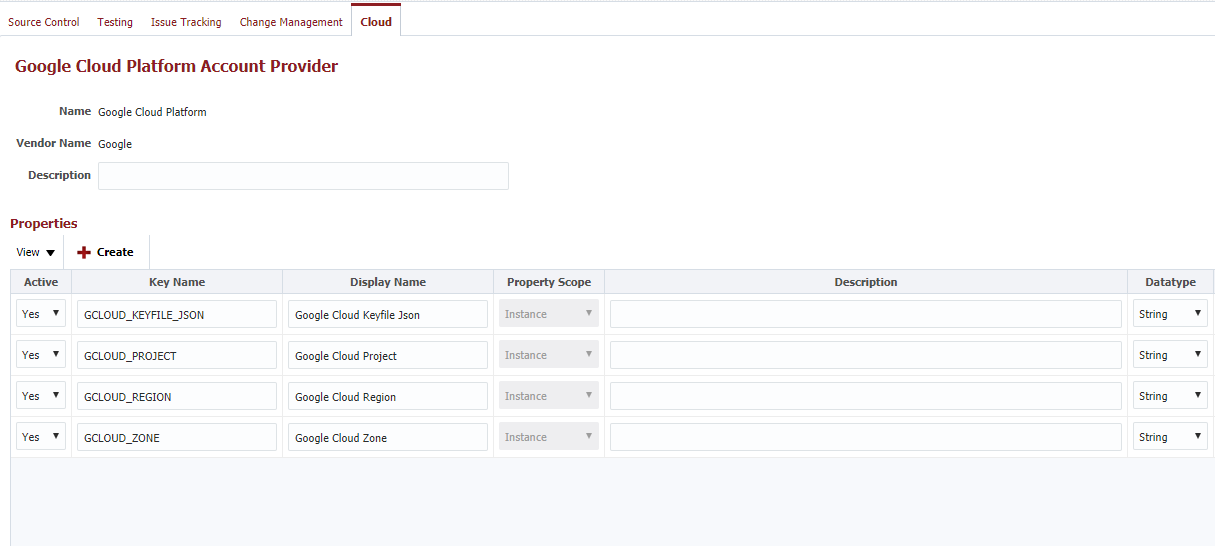
If you wish to use a Provider not in the above supported list you can authenticate using traditional Terraform standards. This usually results in either environment variables for authentication information or having this information directly in the Terraform files. If you wish to use the latter approach you can create a custom FlexDeploy Cloud Account Provider.
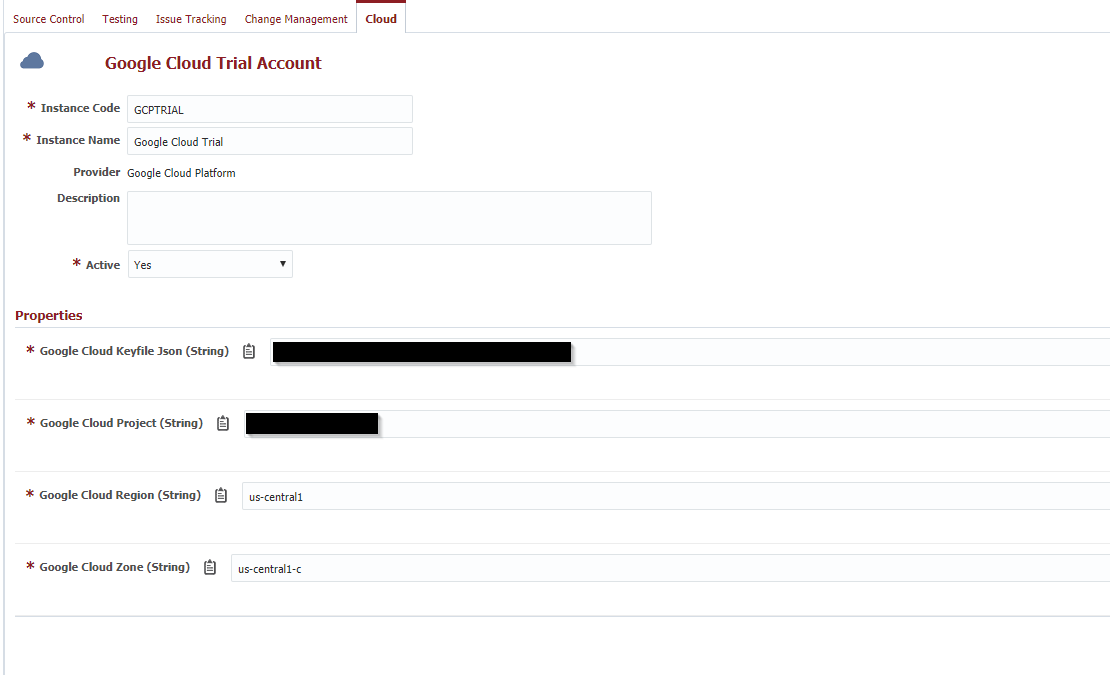
You can then reference the values on the Cloud Account using FlexDeploy properties in your Terraform configuration files. Below I have demonstrated with the Google Cloud Platform provider:
FlexDeploy Provider (Google Cloud Platform)
Flexdeploy Account (Google Cloud Platform)
Terraform Configuration (Google Cloud Platform)
| Code Block | ||||||||
|---|---|---|---|---|---|---|---|---|
| ||||||||
provider "google" {
credentials = "${file("${{GCPJOEL:GCLOUD_KEYFILE_JSON}}")}"
project = "${{GCPJOEL:GCLOUD_PROJECT}}"
region = "${{GCPJOEL:GCLOUD_REGION}}"
zone = "${{GCPJOEL:GCLOUD_ZONE}}"
}
resource "google_compute_instance" "vm_instance" {
name = "terraform-instance"
machine_type = "f1-micro"
boot_disk {
initialize_params {
image = "debian-cloud/debian-9"
}
}
network_interface {
# A default network is created for all GCP projects
network = "${google_compute_network.vpc_network.self_link}"
access_config = {
}
}
}
resource "google_compute_network" "vpc_network" {
name = "terraform-network"
auto_create_subnetworks = "true"
} |