If you are using FlexDeploy 5.2.0.1 or lower version, see Project Security.
In addition to the global permissions configured for Group (on Administration - Security - Groups), FlexDeploy supports a hierarchical permission model for folders, applications, and projects. This permission model allows fine-grained access control to meet any security requirements. Default permissions can be set on the root folder for the entire hierarchy.
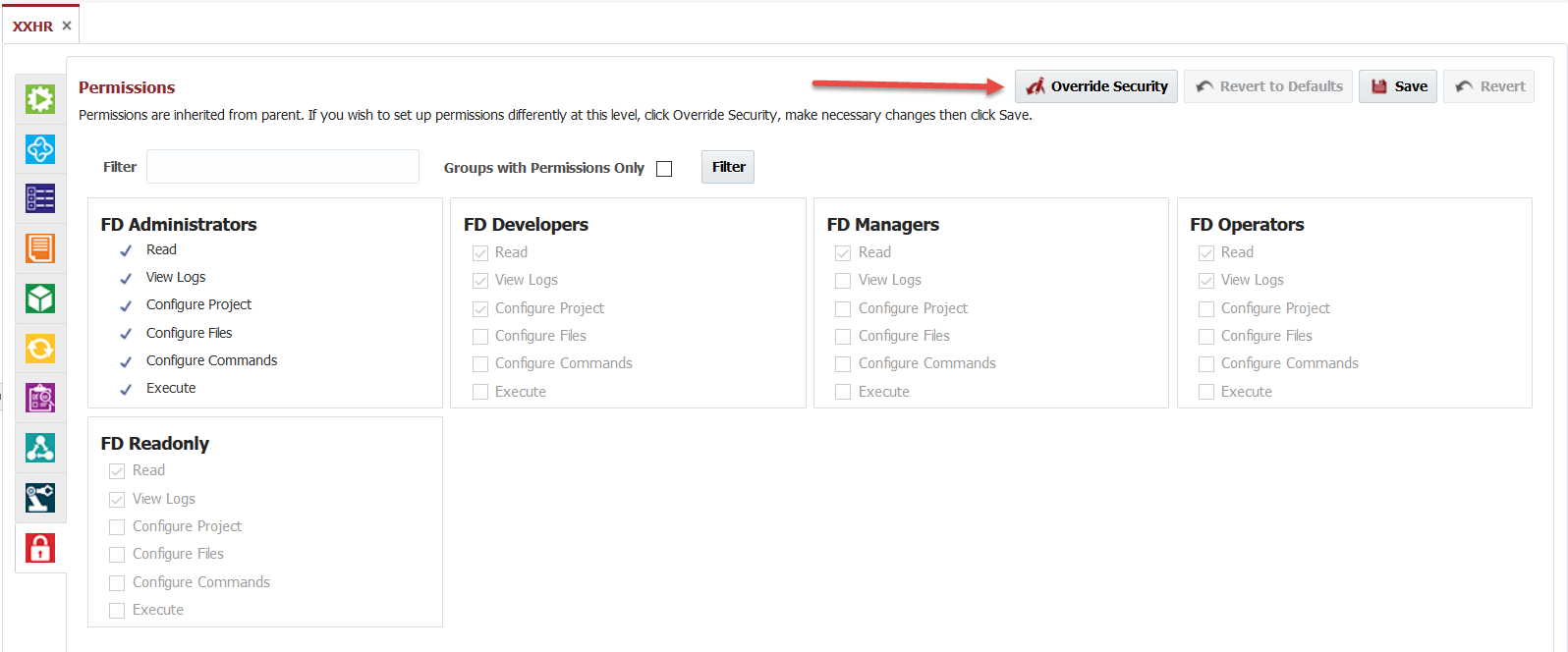
Overriding Security
To override the security permissions, first open a folder, application, or project by double-clicking on it. Then click on the Security tab.
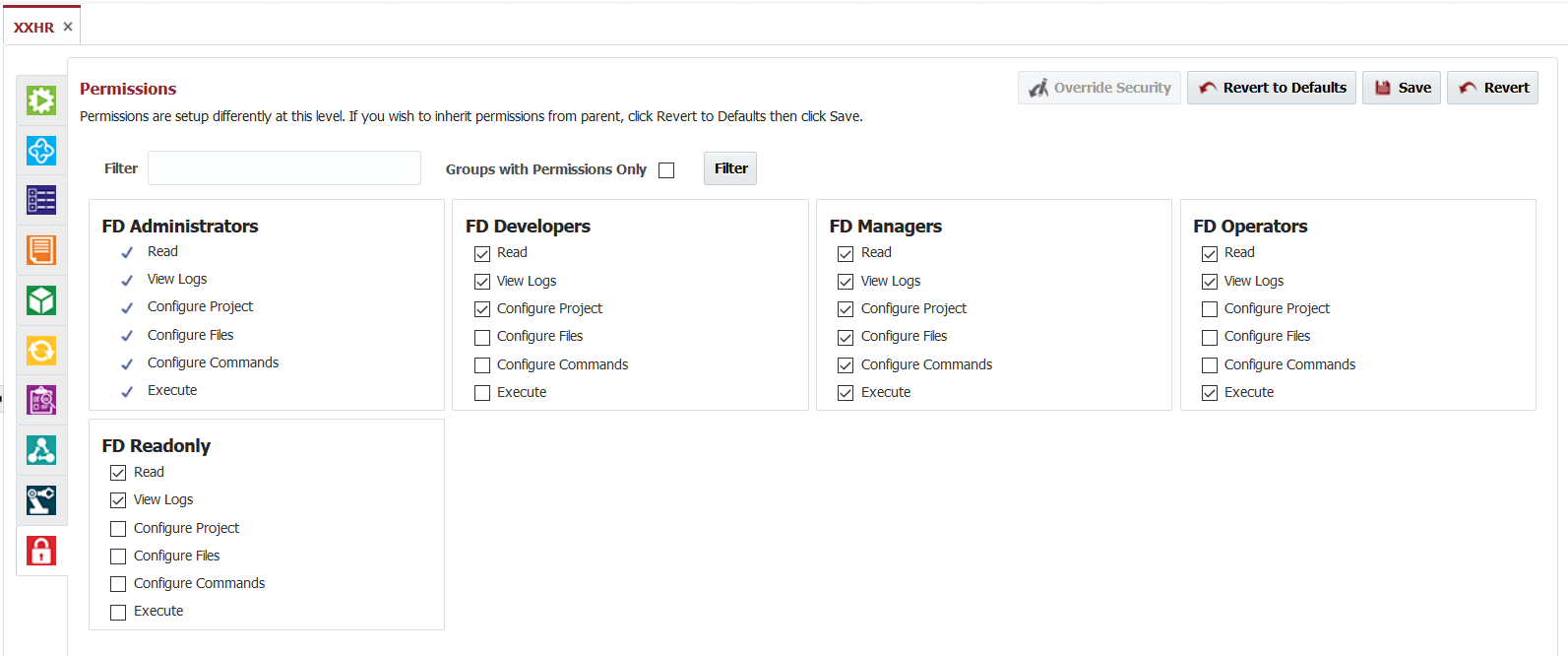
Click the Override Security button to override the permissions of the parent object. Select the permissions you wish to grant for any particular groups, and click the Save button to save any changes.
If there are many Groups in your FlexDeploy installation, you can use the Filter option to limit displayed groups, but when you click Save, all changes are applied irrespective of Filtered display data. For example, if you select values for one group and then filter to find another group and update its settings and then you click Save, changes for both groups will be saved.
At any point, if you decide to inherit permissions from parent again, then click Revert to Defaults and click Save.
The table below provides a summary of the permissions for each object type.
Object Type | Permission | Description |
|---|---|---|
Folder | Read | Grants permission to open objects for viewing. |
View Logs | Grants permission to view logs for underlying executions. | |
Create Folder/Application/Project | Grants permission create objects. | |
Configure Folder/Application | Grants permission to manage objects under configure tab. | |
Execute (Build/Deploy/Test) | Grants permission to execute build/deploy workflows. | |
Application | Read | Grants permission to open objects for viewing. |
View Logs | Grants permission to view logs for underlying executions. | |
Create Folder/Application/Project | Grants permission create objects. | |
Configure Folder/Application | Grants permission to manage objects under configure tab. | |
Execute (Build/Deploy/Test) | Grants permission to execute build/deploy workflows. | |
Project | Read | Grants permission to open project for viewing. |
View Logs | Grants permission to view logs for executions of this project. | |
Configure Project | Grants permission to manage objects under configure tab. | |
| Configure Files | Grants permission to configure Files and its Attributes. Allows for populate of files as well. | |
| Configure Commands | Grants permission to manage Build and Deploy command of files. | |
Execute (Build/Deploy/Test) | Grants permission to execute build/deploy workflows for this project. |
The FlexDeploy permission model offers great flexibility for managing security. However, you must understand that with fine grained security comes the overhead of needing to configure and maintain it. You should avoid managing permissions at a level lower than you really need. For example, if you choose to manage all security at the individual project level, you will need to configure the security every time you create a new project. Instead, if you establish permissions near the top of the folder hierarchy, you will only need to configure security when you create new high-level folders or when your security requirements change.