...
- You must first install and configure HashiCorp Vault if have not already done so.
- Now you can create specific AppRole for FlexDeploy authentication. Use proper role name, for example flexdeploy-role.
AppRole must have policy that allows FlexDeploy to read specific secrets necessary. Note that FlexDeploy only needs read permission. Example policy file
Code Block title Examplay Policy File path "kv/*" { capabilities = ["read", "update"] } path "sys/mounts" { capabilities = ["read"] } path "secret/*" { capabilities = ["create", "read", "update", "delete", "list"] }- You will need role id and secret id for this AppRole for configuration in FlexDeploy.
...
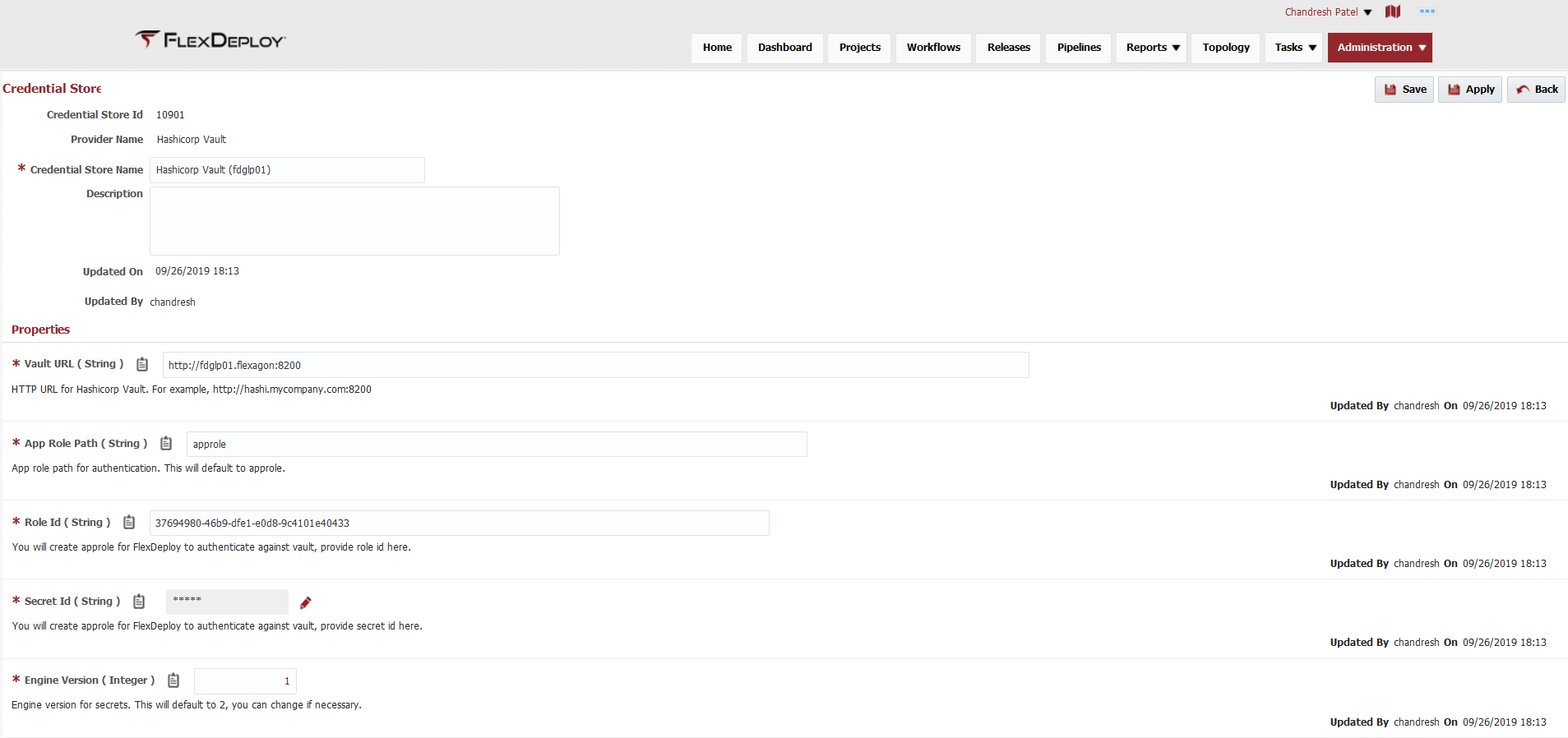
Here are the configurations necessary for this store.
| Property Name | Notes | Example |
|---|---|---|
| Vault URL | HTTP URL for REST service calls. If you use https protocol then make sure to configure KeyStore (default java or application server keystore) with proper certificates. | http://myvault.mycompany.com:8200 |
| App Role Path | App role path for authentication. This will default to approle and it should be sufficient. | approle |
| Role Id | You will create approle for FlexDeploy to authenticate against vault, provide role id here. | as per your Vault configurations |
| Secret Id | You will create approle for FlexDeploy to authenticate against vault, provide secret id here. | as per your Vault configurations |
| Engine Version | Engine version for secrets. This will default to 2, you can change if necessary. | 1 or 2 |
Now you are ready to create individual credential to be retrieved from Vault.
...
HashiCorp Credential requires two inputs as described below. Keep in mind that AppRole created for FlexDeploy must have read access to paths defined by various credentials.
| Input Name | Notes |
|---|---|
| Secrets Path | Path to secrets in HashiCorp Vault. For example, kv/DEV/Database/apps |
| Key Name | Key name for secret value. |
Here is how edit credential looks like.
...