FlexDeploy provides out of box integration with CyberArk AAM to retrieve secrets. FlexDeploy FlexDeploy will authenticate either using client certificate or retrieve credentials using Agent. In this section we will talk about client certificate based authenticationretrieval of credentials using Agent.
CyberArk Setup
- Create necessary Application Id(s) in CyberArk AAM.
- Configure safe and credentials.
- Configure Application Id(s) for specific client certificate authentication.
- If necessary, get PEM files for CyberArk server trustInstall and configure CyberArk Agent on FlexDeploy server. You will need location of clipasswordsdk executable for configuration as well.
FlexDeploy Setup
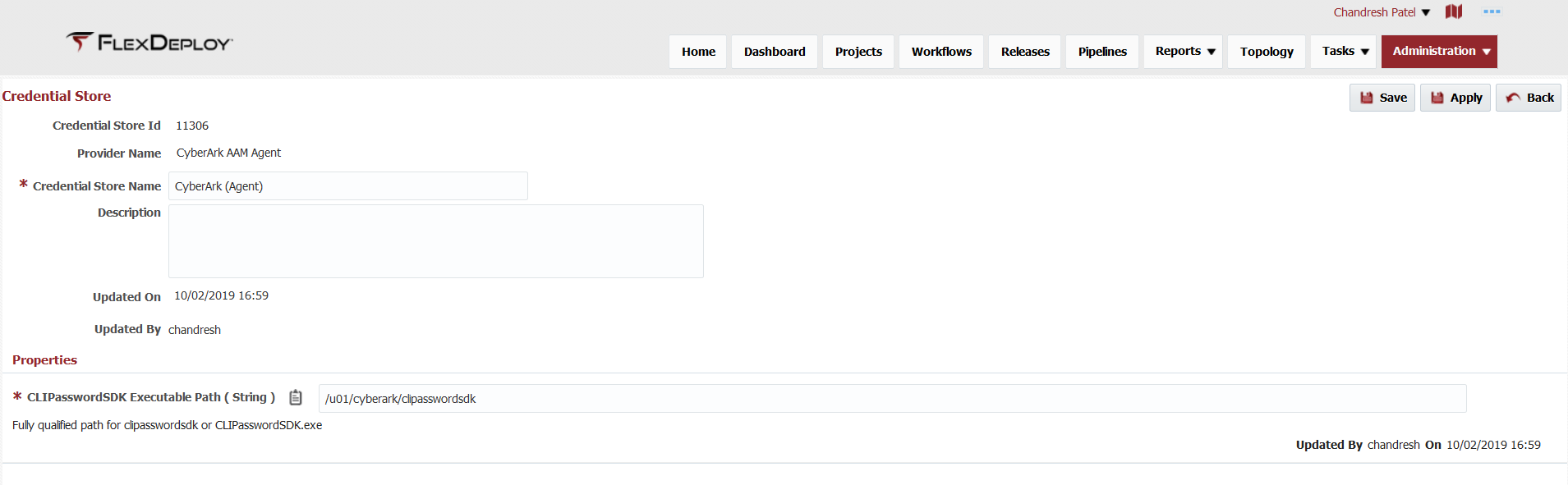
You must first create Credential Store in FlexDeploy by clicking Create Store button on Administration - Security - Credentials page. Credential store represents instance of specific type of credential store provider. If you have more than one CyberArk AAM installations, you will create equal number of Credential Stores in FlexDeploy. Use CyberArk AAM Agent Provider when creating this store.
Here are the configurations necessary for this store.
| Property Name | Notes | Example |
|---|
HTTP URL for CyberArk AAM. FlexDeploy will invoke HTTP GET to retrieve credential. If you use https protocol, then you may have to setup Server Certificate Path.
GET is invoked with URL and path - AIMWebservice/api/Accounts
This private key and certificate is used to authenticate FlexDeploy against CyberArk AAM.
Only PEM certificates are supported at this time. You must store PEM certificate file with private key and certificate on FlexDeploy server in secure location.
Optional, only needed if using https protocol. This certificate is used to setup trust for CyberArk server.
Only PEM certificates are supported at this time. You must store PEM certificate file with certificate on FlexDeploy server in secure location.| CLIPasswordSDK Executable Path | Fully qualified path for clipasswordsdk on Unix or CLIPasswordSDK.exe on Windows. FlexDeploy will invoke this agent script like this.
where APP_ID, QUERY and OUTPUT are inputs configured for each credential. | /u01/cyberark/clipasswordsdk |
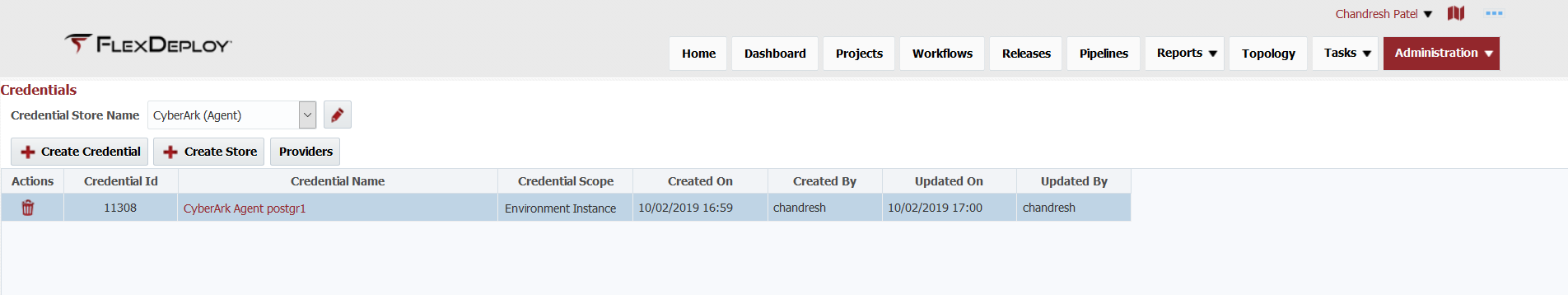
Now you are ready to create individual credential to be retrieved from VaultCyberArk.
You can create or edit credentials from Credentials page or from where specific credential is used.
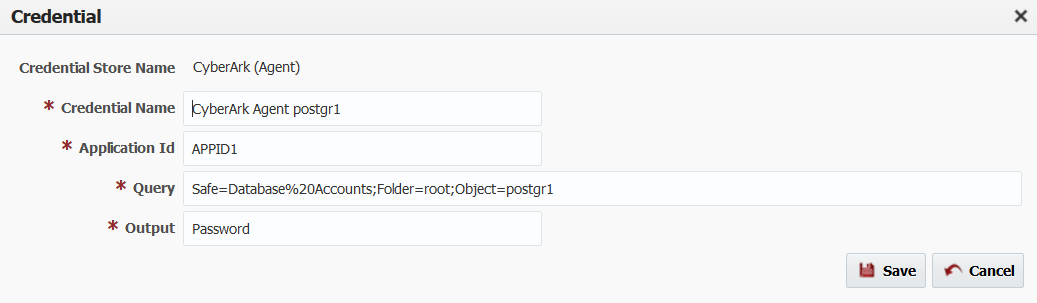
CyberArk credential requires two inputs as described below.
| Input Name | Notes |
|---|---|
| Application Id | Application id and Query Text are used to retrieve secret from CyberArk AAM. |
| Query | Query Text for credential. For example, Safe=Linux%20Accounts;Folder=root;Object=secret |
| Output | This will default to Password. |
Here is how edit credential looks like.
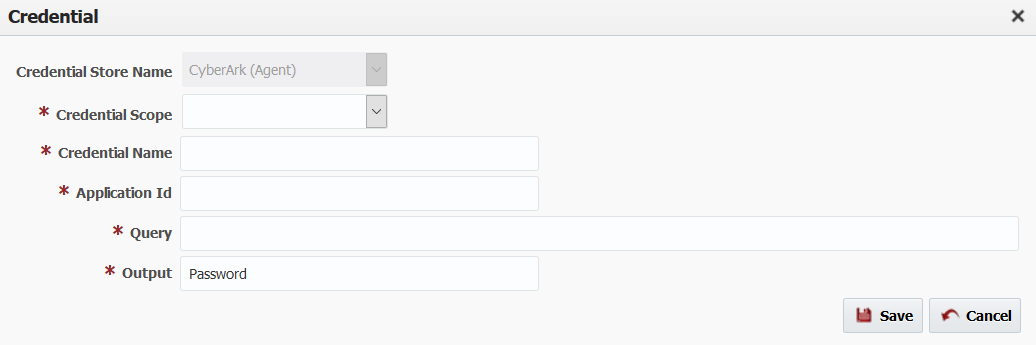
Create credential looks similar except you need to provide Scope as well. Scope can not changed once credential is saved.
You can change credential inputs (Application Id, Query Text) at any point. FlexDeploy will use these inputs with credential store properties like URL, Certificate Path etc. clipasswordsdk to retrieve individual credential for use during Workflow Execution.