| Table of Contents |
|---|
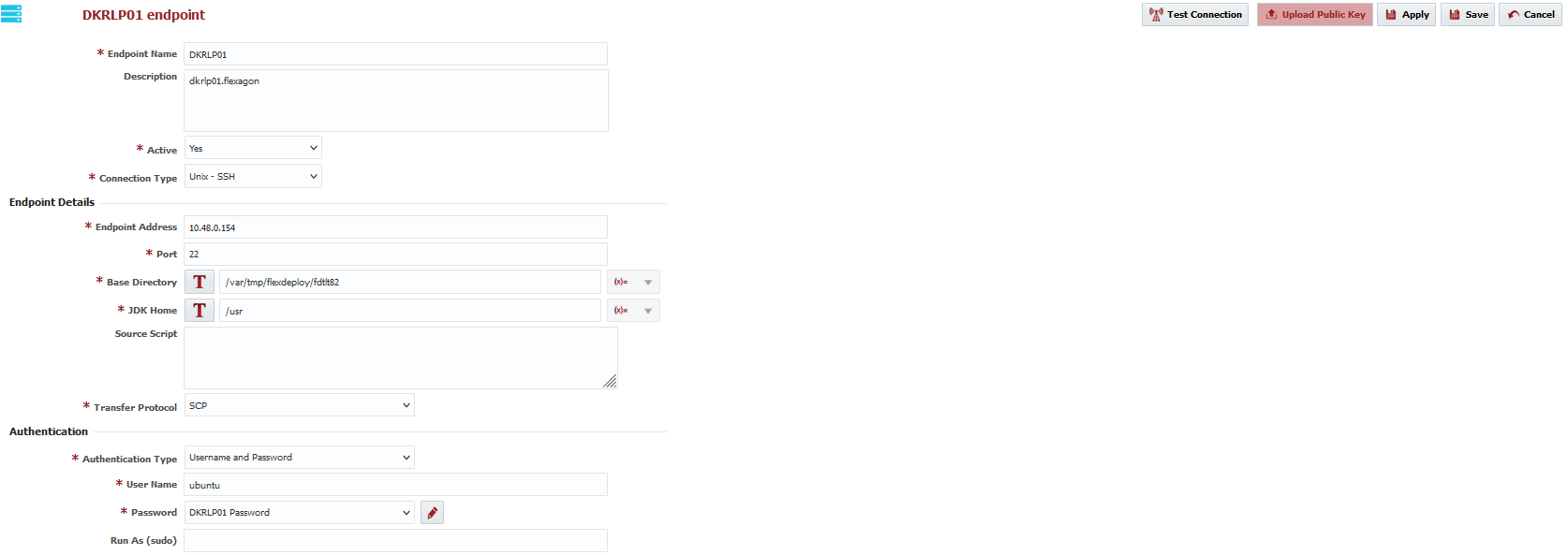
Click the button to create a new Endpoint, or select an existing Endpoint by clicking on the desired row. Enter the required fields as defined in the table below.
| Tip |
|---|
See Endpoint Defaults to setup default values for new Endpoints to save time. |
Field Name | Required | Description |
|---|---|---|
Endpoint Name | Yes | The name of the Endpoint. |
Description | No | An optional description for the Endpoint. |
Active | Yes | Whether or not the endpoint is active in the system. Defaults to "Yes". |
Connection Type | Yes | The connection type used for connection to the Endpoint |
. |
Supports: |
Yes
The operating system of the Endpoint. Unix and Windows are the supported types.
For Microsoft Windows, must have Cygwin installed, along with the openssh package. See /app/flexdeploy.
| ||
| Endpoint Details | ||
Endpoint Address | Yes | The DNS name or IP address of the Endpoint. |
Port | Yes | The SSH port of the Endpoint (typically port 22). |
| Base Directory | Yes | A working directory on the Endpoint used by FlexDeploy. ~ is not supported here. See Permissions information below for details on how to create this folder automatically (Recommended). For example, /app/flexdeploy. If you have two FlexDeploy installations that may connect to same Endpoint, you must use unique folders for both FlexDeploy Servers. In most cases, separate FlexDeploy is installed to perform testing of FlexDeploy patches, which may connect to same Endpoint, in which case you can use different folder like /app/flexdeploytest and /app/flexdeploy. Working directory under /var/tmp or /tmp folder is not recommended as administrators generally have cron jobs to purge files based on age and that will cause issues when plugin files are deleted. For example, Error: Could not find or load main class flexagon.fd.core.plugin.ExternalPluginServer will be encountered when plugin lib files are deleted. Permissions
|
| JDK Home | Yes | The JDK Home directory on the Endpoint. For example, /usr. FlexDeploy will look for /bin/java under specified JDK Home folder. |
| Source Script | No | An optional script executed right before plugins are executed on the endpoint. Script can source some other environment script as well. Script should be Unix shell or Windows bat commands depending on type of Endpoint. If using Windows Cygwin SSH then script should be written as Unix shell. Some usages of this script include sourcing an environment file (. $HOME/mfile.env) or exporting a variable (export FLEXAGON_FD_PLUGIN_JAVA_ARGS="-Xmx1024m -Djava.io.tmpdir=/var/tmp"). Variables exported here will become available to plugin executions on this endpoint. |
| Transfer Protocol | Yes | Protocol/Tool to use to transfer files from FlexDeploy host to endpoint and vice-versa. Options available are:
To use the rsync option, FlexDeploy should be running on a UNIX machine, the endpoint itself can be UNIX or Windows (Cygwin) and rsync needs to be installed on BOTH, FlexDeploy host and endpoint and expect needs to be installed on the FlexDeploy host. |
| Authentication | ||
| Authentication Type | Yes | Mechanism to use for authentication. The Password, Private Key File, and Passphrase are displayed based on selected type. Supports:
|
User Name | Yes | The user account on the Endpoint to connect with. All executions via this endpoint will run as this user. |
Password | No | The password for the User Name. Either password or Private Key File is required. |
Private Key File | No | Fully-qualified path of the SSH private key file on FlexDeploy server. Either Private Key File or Password is required. ~ is not supported here. |
Passphrase | No | An optional passphrase used when the private key was generated. Only valid if a Private Key File is specified. |
Base Directory
Yes
A working directory on the Endpoint used by FlexDeploy. ~ is not supported here.
For example, /app/flexdeploy.
If you have two FlexDeploy installations that may connect to same Endpoint, you must use unique folders for both FlexDeploy Servers. In most cases, separate FlexDeploy is installed to perform testing of FlexDeploy patches, which may connect to same Endpoint, in which case you can use different folder like /app/flexdeploytest and| Run As (sudo) | No | An optional user to run as (using sudo) after establishing connection to the endpoint when working with Unix OS.
If there is a need to adjust sudo commands, then it can be done by setting up description value like shown below. Please consult with Flexagon support if questions on this topic.
Note that there is space at the end of each line. Both prefix and suffix should be on it's own line in Description input. In this example, FlexDeploy will run sudo as per this example command: “ | ||
| Group | No | An optional group identifier which can be useful when searching for Endpoints. | ||
| Subgroup | No | An optional subgroup identifier which can be useful when searching for Endpoints. |
JDK Home
The JDK Home directory on the Endpoint. For example, /usr/java. FlexDeploy will look for /bin/java under specified JDK Home folder.
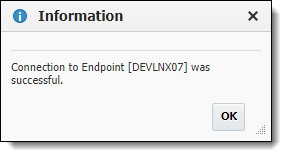
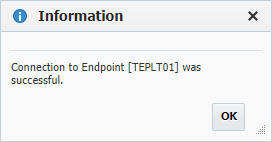
Optionally, click the Test Connection button to validate that the FlexDeploy server can connect to the configured Endpoint.
Click the Save button to save the changes to the Endpoint. Optionally click the Apply button to save the changes, but remain on the current screen until the Cancel button is clicked.
To inactivate an endpoint click the Active link on the desired Endpoint, and it will toggle to Inactive. This will hide that Endpoint after leaving the screen, until the Active checkbox is unchecked. To reactivate an Enpoint, click the Inactive link and it will toggle back to Active. This endpoint is now active in the system again and ready for use.
SSH Authentication
FlexDeploy utilizes SSH to connect to its configured Endpoints. SSH uses public-key cryptography to authenticate the remote computer and allow it to authenticate the user. FlexDeploy FlexDeploy supports Creating an SSH Endpoint and Creating an SSH Endpoint.Starting with 4.5.2, using Password Authentication or using SSH Keys.
FlexDeploy also supports using sudo user. At this point User Interface does not have separate entry for sudo user, next release will provide better user experience for sudo user setup. See Configure sudo user for Unix EndpointSee Run As (sudo) details above.
Supported Algorithms for SSH
| Tip |
|---|
Flexagon focuses its testing with RSA keys for SSH, since their use is more prevalent by our customers. We therefore recommend using RSA. |
| Include Page | ||||
|---|---|---|---|---|
|
Password AuthenticationAnchor PasswordAuth PasswordAuth
| PasswordAuth | |
| PasswordAuth |
The first mechanism is to use automatically generated public-private key pairs to simply encrypt a network connection, and then use password authentication to log on. In this case you must provide a User Name and Password to connect to the endpoint.
| Unix Example | Windows Example (using Cygwin) | ||
|---|---|---|---|
| Tip | ||
|---|---|---|
| ||
MacOS endpoints are supported using Unix Connection Type. |
Public-Private Key AuthenticationAnchor ppk ppk
| ppk | |
| ppk |
The second technique is to use a manually generated public-private key pair to perform the authentication, allowing the FlexDeploy server to connect to endpoints without having to specify a password. In this scenario, a public and private key pair are generated on the FlexDeploy server. The private key is kept secretly on the server by setting the permissions such that only the owner can read it (the userid which the FlexDeploy server is running as). The public key is copied to all endpoint computers which must allow access to the owner (user running FlexDeploy server) of the matching private key. While authentication is based on the private key, the key itself is never transferred through the network during authentication. SSH verifies whether the same person offering the public key also owns the matching private key. In this case you must provide the User Name, the path to the Private Key File on the server, and an optional Passphrase (an optional password assigned to the private key when it was generated).
Creating a Public-Private Key Pair
If you do not already have SSH keys generated for the host where FlexDeploy is installed, login (or switch user) as the user which FlexDeploy runs as, and run the following OpenSSH command.
| Tip |
|---|
Flexagon focuses its testing with RSA keys for SSH, since their use is more prevalent by our customers. We therefore recommend using RSA. |
- ssh-keygen –t -t <rsa | dsa> ** where rsa or dsa is the encryption algorithm you wish to use. For example,
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
ssh-keygen -t rsa
OR
ssh-keygen -t dsa |
Here is the sample output (with interactive prompts) using rsa encryption.
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
Generating public/private rsa key pair. Enter file in which to save the key (/home/oracle/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/oracle/.ssh/id_rsa. Your public key has been saved in /home/oracle/.ssh/id_rsa.pub. The key fingerprint is: e4:dd:6d:88:e0:64:9c:3e:9d:f7:7d:6f:2e:56:dd:6b oracle@devlnx12 The key's randomart image is: +--[ RSA 2048]----+ | | | . . | | B | | B + + o | | S = + o o| | . . o .+| | ..+| | oE+| | ..+o| +-----------------+ |
It is typical to use the default file name and location to store the private key (which is in the .ssh subfolder of the user's home directory). You can optionally secure the private key file with a passphrase. It is an SSH requirement that the private key be readable only by its owner (e.g. oracle in the example above). So you must change the permissions accordingly (e.g. chmod 600 /home/oracle/.ssh/id_rsa). You will receive an error at connection time similar to the following if you omit this step.
Permissions 0777 for '/home/oracle/.ssh/id_rsa' are too open.
It is recommended that your private key files are NOT accessible by others otherwise private key will be ignored.
| Tip |
|---|
The /home/oracle/.ssh folder on the endpoint must have drw------- permissions. For example,
|
Uploading the Public Key
We must now copy the contents of the public key to each endpoint host. This step can be performed manually or using FlexDeploy UI. To save time and avoid errors, use Upload Public Key button on FlexDeploy UI for specific Endpoint.
...
The public key can also be copied to the endpoint's authorized_keys file using the Upload Public Key button.
Validate that the derived name and location of the public key is correct, and enter the password for the Endpoint connection user (if not already provided on the Endpoint definition). Click the Upload button to upload the public key to the Endpoint.
Configure sudo user for Unix Operating System
FlexDeploy 4.6 supports use of sudo user for Unix Endpoint. FlexDeploy 4.5 patch release also supported sudo, but now configurations of sudo user is much simplified. Using this approach you can setup Endpoint with user "dan" but eventually sudo to user "oracle".
...
- Test by executing following from terminal as service account – “sudo -u <user> bash -c whoami”
- It should print the run as user name without prompting for a password
...
Special Note for Oracle Java Cloud Service
The SSH connectivity for the Java Cloud Service is no different than when running on-premise. However, by default you will not know the password for the oracle user. You have two options for configuring endpoints on Java Cloud Service instances.
...