...
| Info | ||
|---|---|---|
| ||
User record must exist in FlexDeploy even for External Realm Users. This is necessary so that user can control Notification settings and allows Administrator to provide additional Security if necessary. When users defined in External Realm logs in successfully first time, a new User record in created in FlexDeploy. At this point user is asked to provide various information like First Name, Last Name, Email etc. Password for such users is always managed in External Server. Once user provides necessary details, automatic logout will occur and user will have to perform login one more time. At this point, user will be granted access based on Realm Group Mapping configured by Administrator, which is explained later in this document. |
Create LDAP Realm
To create an LDAP Realm click the Create button and Select LDAP Realm.
...
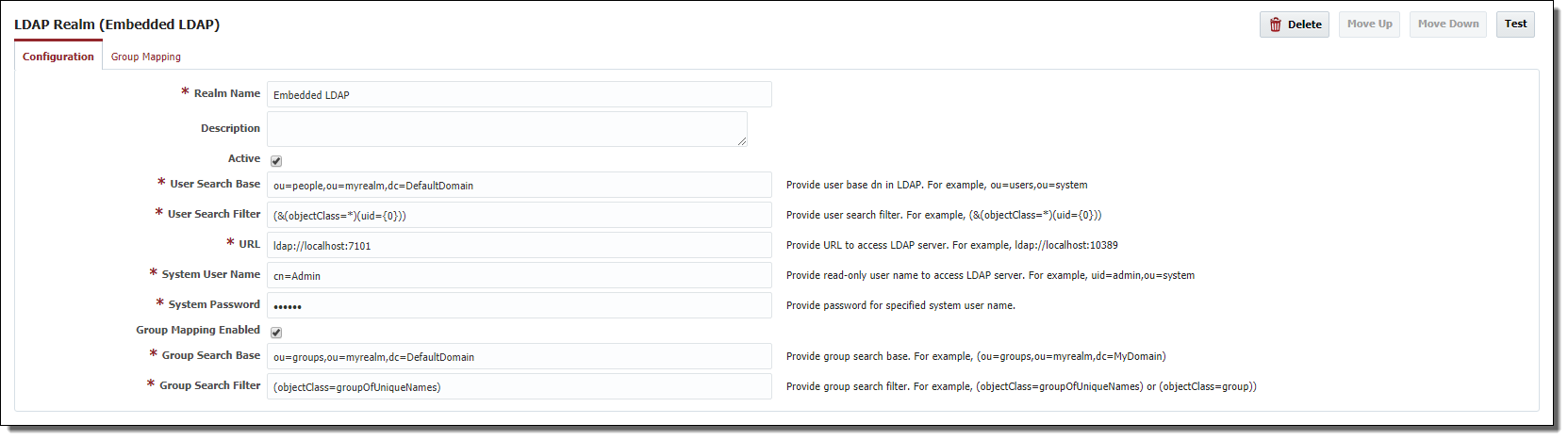
WebLogic Embedded LDAP Realm Example
Apache Directory Server Realm Example
...
Field | Required | Description |
|---|---|---|
Realm Name | Yes | Name of the LDAP Realm. |
Description | No | Description of the realm. |
Active | Yes | Whether the realm is active or not. Default is Active. |
User Search Base | Yes | Provide User base tree in LDAP server. For example, ou=users,ou=system. |
User Search Filter | Yes | Provide User search filter to find user records in User Search Base. For example, (&(objectClass=*)(uid={0})) |
URL | Yes | Provide URL to access LDAP server. For example, ldap://localhost:10389 |
System User Name | Yes | Provide read-only user name to access LDAP server. For example, uid=admin,ou=system |
System Password | Yes | Provide password for specified system user name. |
Group Mapping Enabled | No | Check if you want to map LDAP groups to FlexDeploy groups. LDAP server must support memberOf attribute for group mapping in FlexDeploy. |
Group Search Base | No | Provide Group base tree in LDAP server. For example, ou=groups,ou=system. |
Group Search Filter | No | Provide search filter to find groups in Group Search Base. For example, (objectClass=groupOfUniqueNames) |
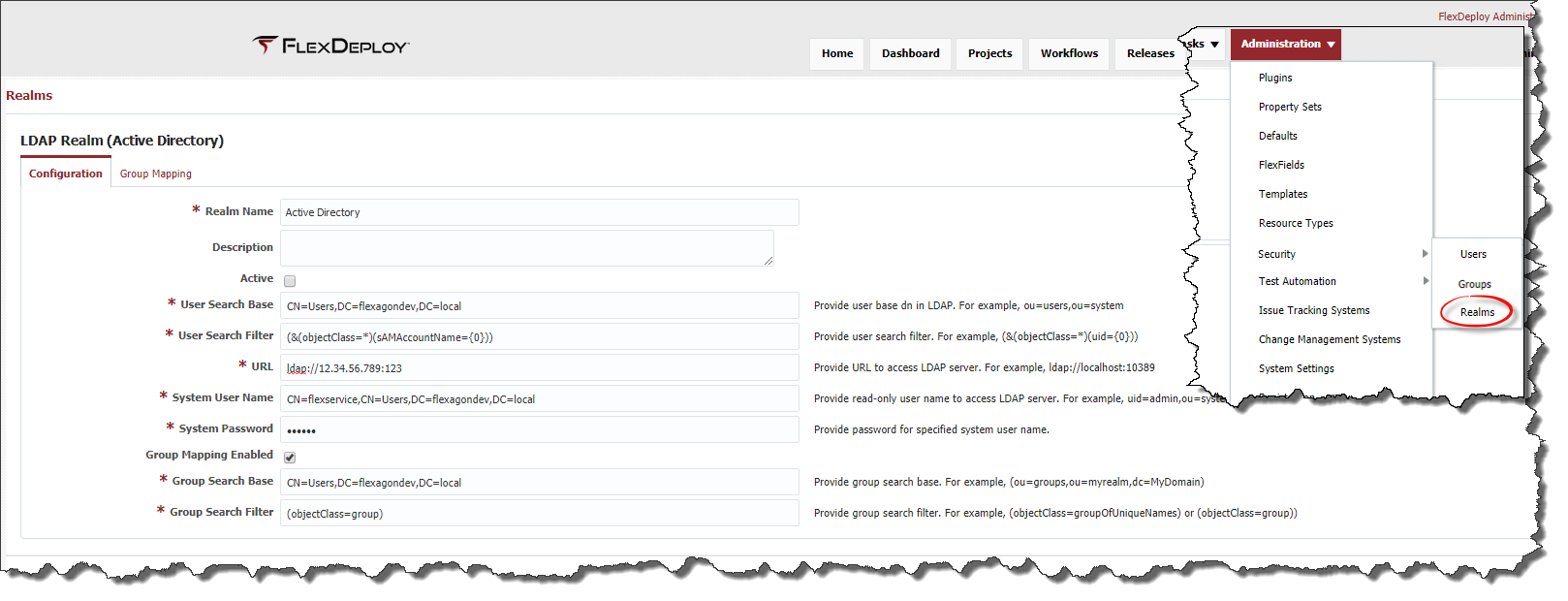
Create Active Directory Realm
...
Field | Required | Description |
|---|---|---|
Realm Name | Yes | Name of the Active Directory realm. |
Description | No | Description of the realm. |
Active | No | Whether the realm is active or not. Default is Active. |
User Search Base | Yes | Provide the user base dn in the Active Directory server. For example, CN=Users,DC=flexagondev,DC=local. |
User Search Filter | Yes | Provide the user search filter. For example, (&(objectClass=*)(sAMAccountName={0})) |
URL | Yes | Provide URL to access active directory server. For example, ldap://localhost:10389 |
System User Name | Yes | Provide read-only user name to access active directory server. For example, CN=flexservice,CN=Users,DC=flexagondev,DC=local |
System Password | Yes | Provide password for specified system user name. |
Group Mapping Enabled | No | Check if you want to map active directory groups to FlexDeploy groups. |
Group Search Base | No | Provide Group base tree in active directory server. For example, CN=Groups,DC=flexagondev,DC=local . |
Group Search Filter | No | Provide search filter to find groups in Group Search Base. For example, (objectClass=group) |
Group Mapping with External Directory ServerAnchor GroupMapping GroupMapping
| GroupMapping | |
| GroupMapping |
FlexDeploy provides features to map external directory server groups to FlexDeploy groups, which makes it very easy to manage FlexDeploy users in your environment. Fine-grained access to FlexDeploy features is still controlled by FlexDeploy groups, and by mapping external directory groups to FlexDeploy groups, you essentially control access to FlexDeploy features. You can configure FlexDeploy group permissions using Groups screen and Security tab on each Application/Folder/Project tab on project tree structure.
...
.
In order to setup Group mapping, check Group Mapping Enabled checkbox, then select Group Mapping tab. Select specific group in External Groups and shuttle desired FlexDeploy groups to Mapped FlexDeploy Groups. See the figure below, where we have mapped Active Directory Group FDDevelopers to FD Developers and Embedded WebLogic group Administrators to FD Administrators.
...