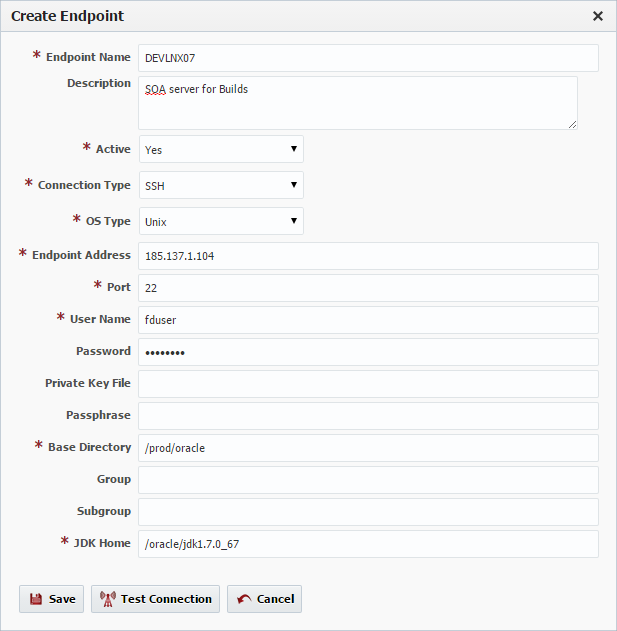
Click the Create button to create a new Endpoint, or select an existing Endpoint and click the Edit button to edit an existing endpoint. Enter the required fields as defined in the table below.
Field Name | Required | Description |
|---|---|---|
Endpoint Name | Yes | The name of the Endpoint. |
Description | No | An optional description for the Endpoint. |
Active | Yes | Whether or not the endpoint is active in the system. Defaults to "Yes". |
Connection Type | Yes | The connection type used for connection to the Endpoint. Currently SSH and localhost are supported. |
OS Type | Yes | The operating system of the Endpoint. Unix and Windows are the supported types. |
Endpoint Address | Yes | The DNS name or IP address of the Endpoint. |
Port | Yes | The SSH port of the Endpoint (typically port 22). |
User Name | Yes | The user account on the Endpoint to connect with. |
Password | No | The password for the User Name. Either password or Private Key File is required. |
Private Key File | No | Fully-qualified path of the SSH private key file. Either Private Key File or Password is required. ~ is not supported here. |
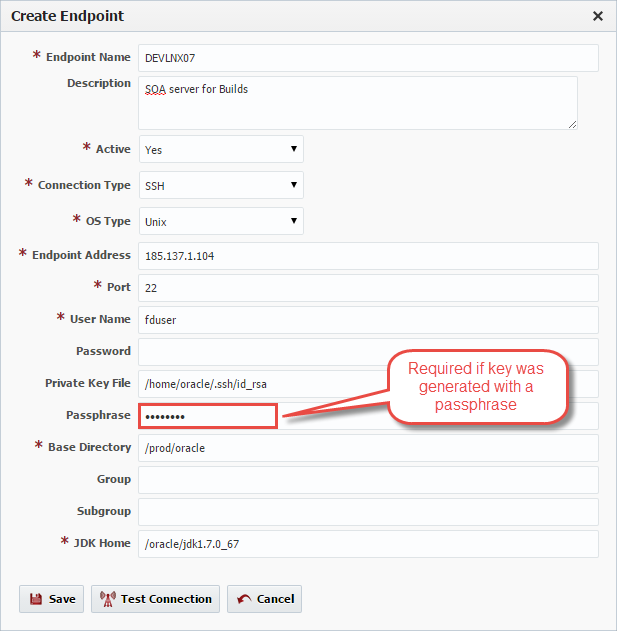
Passphrase | No | An optional passphrase used when the private key was generated. Only valid if a Private Key File is specified. |
Base Directory | Yes | A working directory on the Endpoint used by FlexDeploy. ~ is not supported here. |
Group | No | An optional group identifier which can be useful when searching for Endpoints. |
Subgroup | No | An optional subgroup identifier which can be useful when searching for Endpoints. |
JDK Home | Yes | The JDK Home directory on the Endpoint. |
Optionally, click the Test Connection button to validate that the FlexDeploy server can connect to the configured Endpoint.
...
FlexDeploy utilizes SSH to connect to it its configured Endpoints. SSH uses public-key cryptography to authenticate the remote computer and allow it to authenticate the user. FlexDeploy supports two SSH authentication mechanisms as described below Password Authentication and Public-Private Key Authentication.
Password AuthenticationAnchor PasswordAuth PasswordAuth
| PasswordAuth | |
| PasswordAuth |
The first mechanism is to use automatically generated public-private key pairs to simply encrypt a network connection, and then use password authentication to log on. In this case you must provide a User Name and Password to connect to the endpoint.
Public-Private Key AuthenticationAnchor ppk ppk
| ppk | |
| ppk |
The second mechanism is to use a manually generated public-private key pair to perform the authentication, allowing the FlexDeploy server to connect to endpoints without having to specify a password. In this scenario, a public and private key pair are generated on the FlexDeploy server. The private key is kept secretly on the server by setting the permissions such that only the owner can read it (the userid which the FlexDeploy server is running as). The public key is copied to all endpoint computers which must allow access to the owner (user running FlexDeploy server) of the matching private key. While authentication is based on the private key, the key itself is never transferred through the network during authentication. SSH verifies whether the same person offering the public key also owns the matching private key. In this case you must provide the User Name, the path to the Private Key File on the server, and an optional Passphrase (an optional password assigned to the private key when it was generated).
Creating a Public-Private Key Pair
If you do not already have SSH keys generated for the host where FlexDeploy is installed, login (or switch user) as the user which FlexDeploy runs as, and run the following OpenSSH command.
...
It is typical to use the default file name and location to store the private key (which is in the .ssh subfolder of the user's home directory). You can optionally secure the private key file with a passphrase. It is an SSH requirement that the private key be readable only by its owner (e.g. oracle in the example above). So you must change the permissions accordingly (e.g. chmod 600 /home/oracle/.ssh/id_rsa). You will receive an error at connection time similar to the following if you omit this step.
Permissions 0777 for '/home/oracle/.ssh/id_rsa' are too open.
It is recommended that your private key files are NOT accessible by others.
This private key will be ignored.
The /home/oracle/.ssh folder on the endpoint must have drw------- permissions (eg. chmod 700 /home/oracle/.ssh)
...